In Part 2 of the "Phishing Attacks and Recommended Solutions to Protect Your Organization" webinar we are going to be reviewing the first anti-phishing solution – Mimecast. This is the solution we presently protect ourselves with here at Akins IT and has an excellent suite of tools that extends even further than phishing. In this blog we will be reviewing Platform Type, Requirements to Implement, Security Measures in the Targeted Threat Protection suite, User Training, and some other considerations, including, integration with other services.
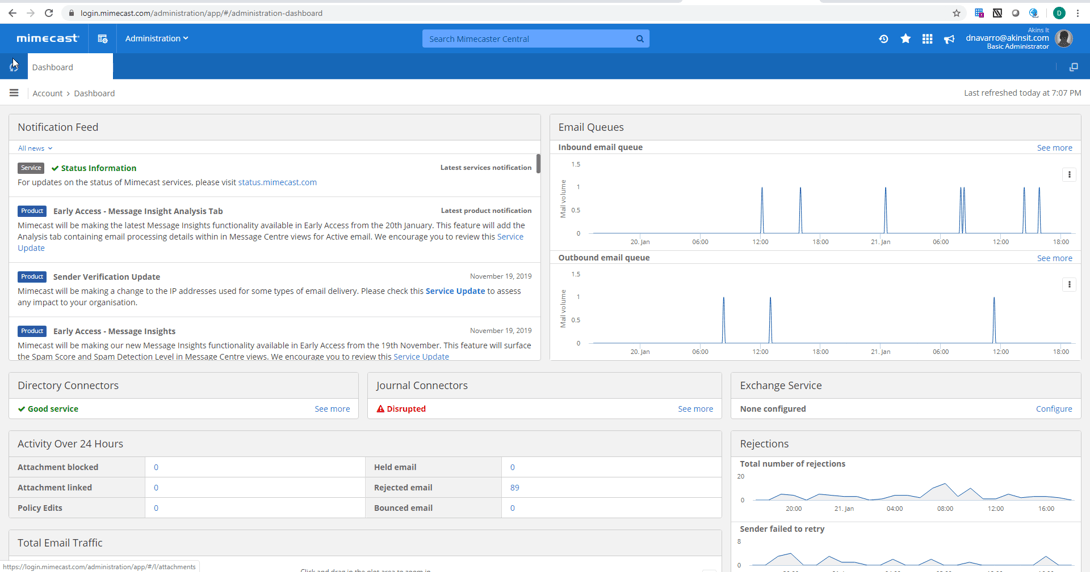
In the image below, you can see the Mimecast Administration Dashboard. The portal gives us visibility on email queues, activity over the last 24 hours, total email traffic and rejections. This allows you the ability to quickly identify any abnormalities with your services, such as an outage, which would cause your inbound and outbound email queue to rise. This operates on a Software as a Service Platform, which on a high-level means that there is no management of the software or hardware; and it is provided as a cloud solution through a web interface. In terms of requirements – there are none for implementation and this solution is available for any email system.
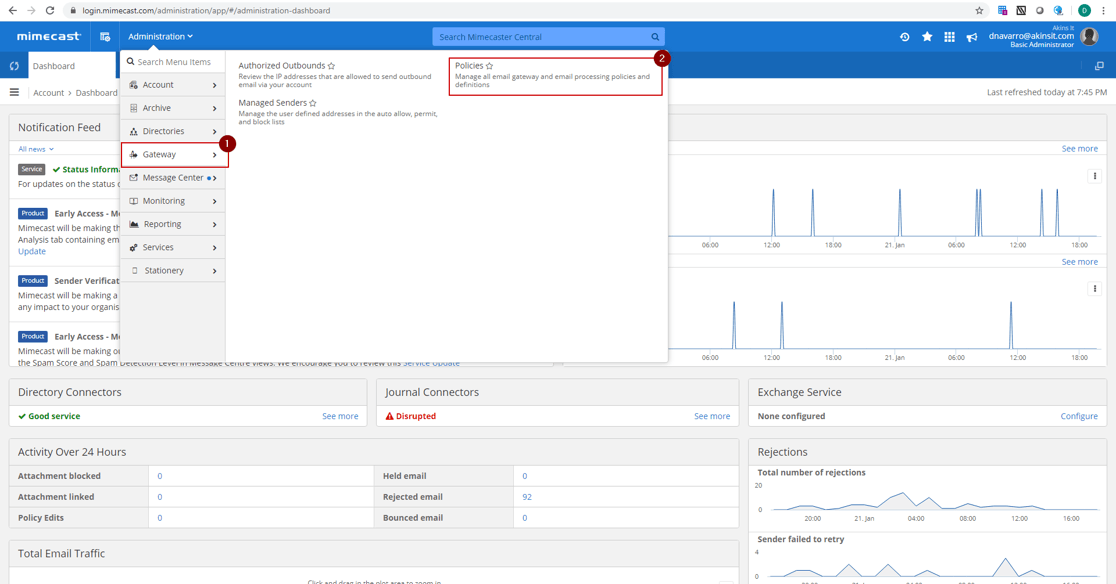
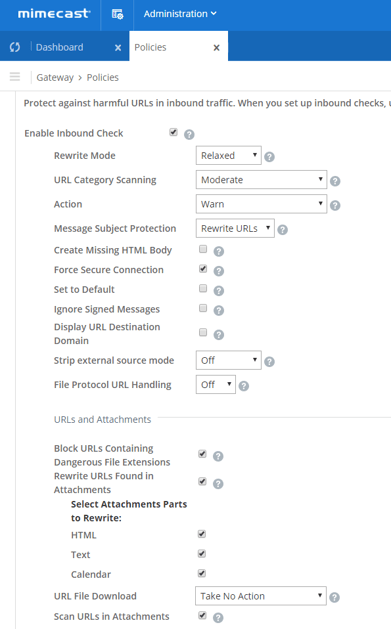
Heading into Administration Menu > Gateway > Policies you will be able to find the policies that we are reviewing. For Anti-Phishing and other targeted attacks, you will utilize the Targeted Threat Protection suite.
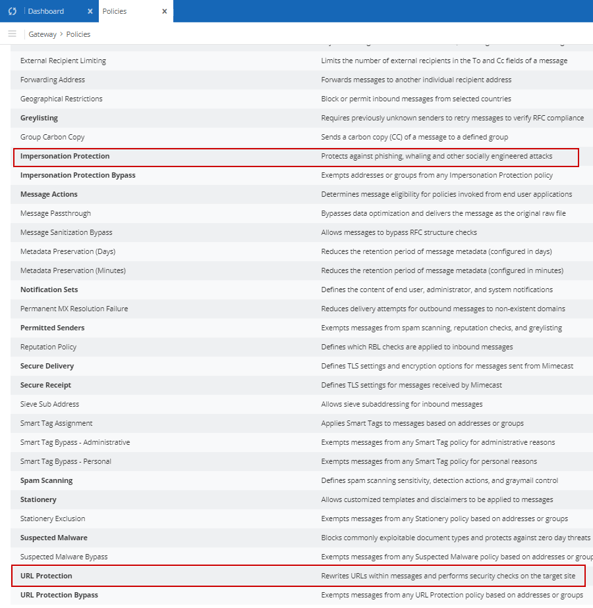
Here we can see the plethora of policies available for configuration to fine tune this for your organization. Emphasized by the red boxes are the policies that target phishing specifically. So on a high level, what do these do?
TARGETED THREAT PROTECTION
What Mimecast provides with URL protect is the ability to rewrite URLs found in emails, including URLs in attachments, and provide real-time scanning with every click on any device. This is all achieved by rewriting URLs in emails into a Mimecast URL that directs users to a Mimecast landing page where a layered security check is performed on the destination site. This check reviews blacklists, real-time feeds, cached feeds, performs heuristic analysis and domain impersonation detection. If Mimecast finds the site to be malicious, you can control how users will be able to proceed, as well as use this opportunity to educate users. More on this subject available in User Training.
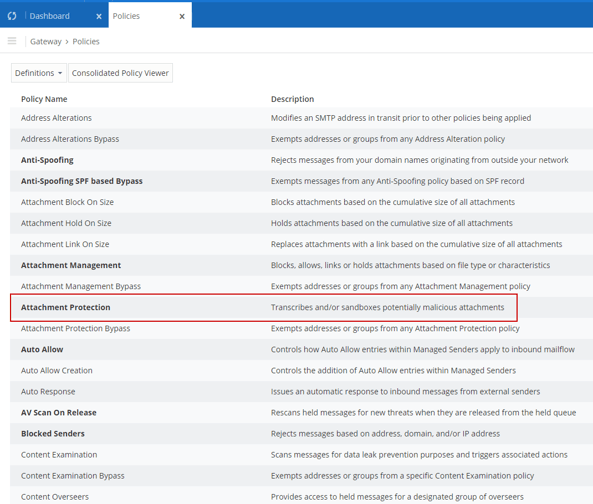
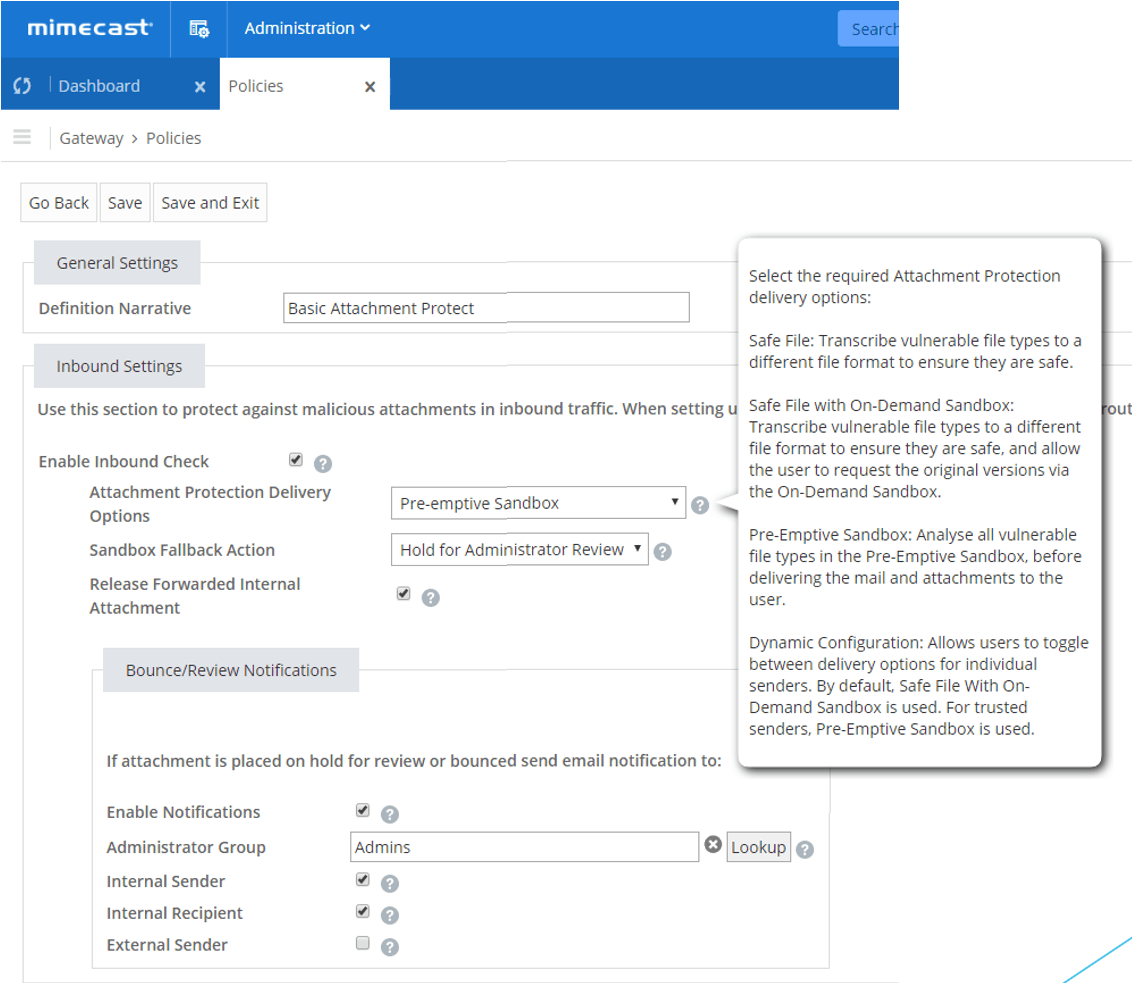
Moving into Attachment protect, we begin looking into how we protect attachments sent to users. Mimecast provides Safe File, Safe File on-Demand Sandbox, Preemptive Sandbox, and Dynamic Configuration.
With Safe File – we take attachments that could contain malicious code and replace them with safe versions. This allows for immediate delivery of attachments and in cases where the original file is needed employees can request for the original file where it is scanned on-demand before delivery.
With Preemptive Sandbox – we can break down attachments using full system emulation and virtualization to open the file and perform a deep security analysis to spot malicious activity at code level and detect malicious actions in executable and non-executable code. If the file is deemed safe, the mail is delivered to the recipient.
Lastly Dynamic Configuration – allows users to control deliver options based on the sender. It uses Safe File with on-demand delivery by default and then preemptive sandbox for trusted sender. This providing the ability to combine the above features and ability for emails to be delivered instantly with no delays.
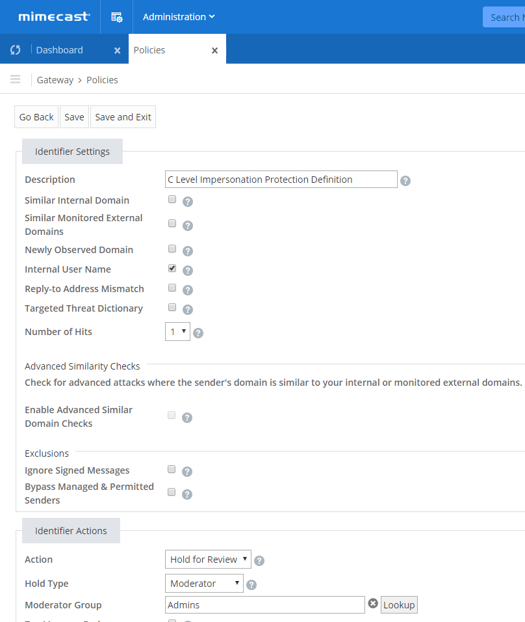
Lastly with the Targeted Threat Protection suite, we look at Impersonation protect. This service provides the ability for real time scanning of all inbound emails to detect header anomalies, domain similarity, recency of the sending domain, and sender spoofing. You can add the names of key users and prevent mail from being delivered when a match comes through. Here you see a typical Schedule C definition where you have a direct check against the Internal Username and a requirement of 1 hit to be subject to hold. It would be recommended to compliment this with a general policy that checks for more hits but with an increased tolerance to prevent false positives.
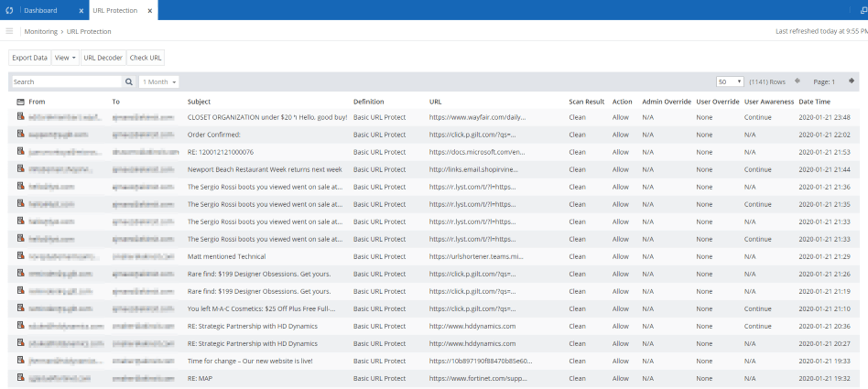
Here we can see monitoring capabilities of URL protect – but the same applies to Impersonation and Attachment Protect, as well as others. With this you can evaluate mail and confirm if the policy configurations are a good fit with your organization – as well as get a deeper analysis on the specifics of Mimecast’s findings.
USER TRAINING
In many ways, you must think that the saying "you are as strong as your weakest link" applies when you think about your cybersecurity risks. While the polices we just discussed do strongly reduce your chances of a successful phishing attack– your last layer of defense is your users. An important fundamental concept to apply here is when you analyze the anatomy of a successful cyberattack. Nearly all of them have one thing in common – A user somewhere did something that could been avoided. Mimecast has a product dedicated to Awareness training but also incorporates this into some policies we previously discussed.
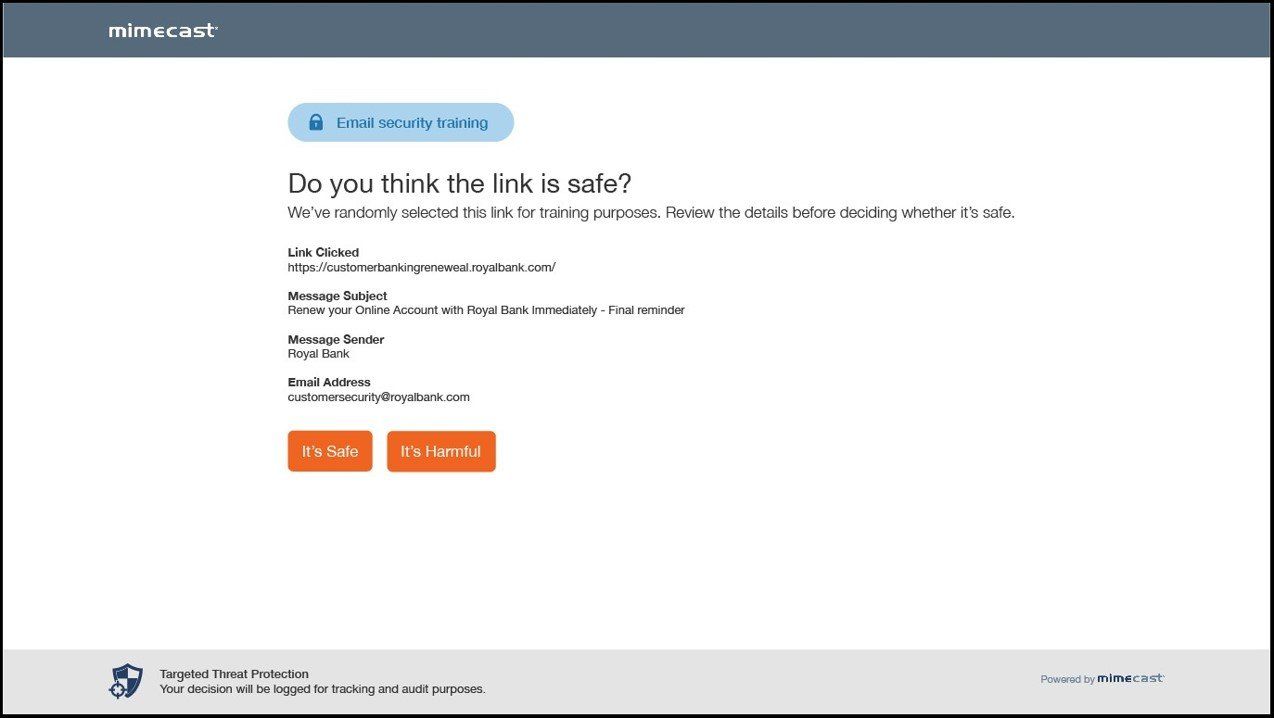
One example of this, as I alluded to earlier, is with URL Protect. When a user clicks on a link, you can configure the ability to occasionally and randomly test users on whether the link they clicked was safe or not. This allows admins to go back later and provide training with the user on where they may have gone wrong without any of the consequences.
OTHER CONSIDERATIONS
Some Integration with other services includes:
- Active directory sync with On-prem exchange
- Office 365
- Azure Active Directory
- Gsuite
- and is compatible with Single Sign On
Additionally, Mimecast has a growing library of API & Tech Partners to compliment this SaaS solution. Some of these include:
- Salesforce
- ConnectWise
- Segasec
The full list can be found at https://www.mimecast.com/tech-connect/tech-partners/
n addition to the integration with other services – and when speaking outside of phishing, some consideration with Mimecast would also include mailbox continuity, information archiving, secure messaging, and a personal portal for your users.
ADVANTAGES
Some advantages you find here that you don’t find in a majority of other solutions is the focus on User training. Advantages include the personal portal for end users to curate and control safe list, blocked lists, and depending on policies – configured user holds to release their own mail. This tied with SSO providing a seamless experience your end users. And lastly, Mailbox Continuity to prevent mail loss due to outages.
CONCLUSION
If you found the above information valuable and would like to see how Mimecast can enhance your email security in your organization, contact us.