microsoft 365 security
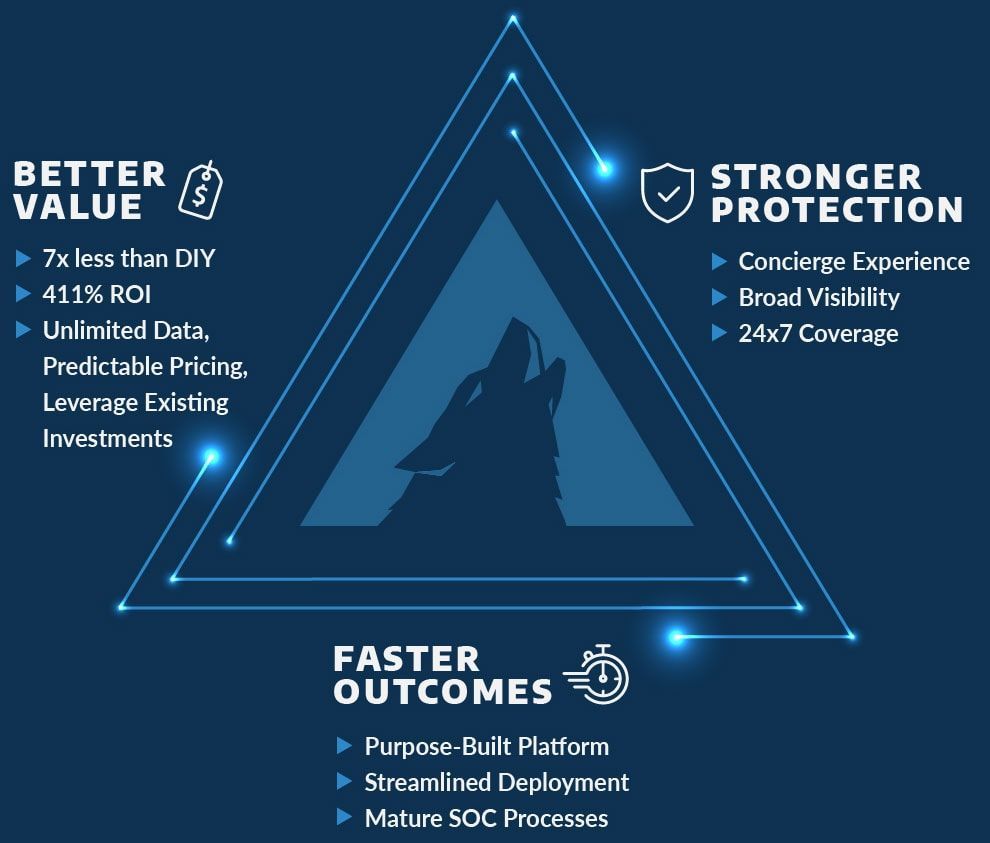
At Akins IT, we understand the critical importance of safeguarding your organization's digital assets. Our suite of security solutions is designed to provide robust protection across all aspects of your Microsoft 365 environment. From risk assessments to advanced threat protection, we offer a range of services to ensure your data remains secure and compliant. Explore the sections below to learn more about how our solutions can help you mitigate risks, enhance security, and maintain compliance.
M365 Risk Assessment
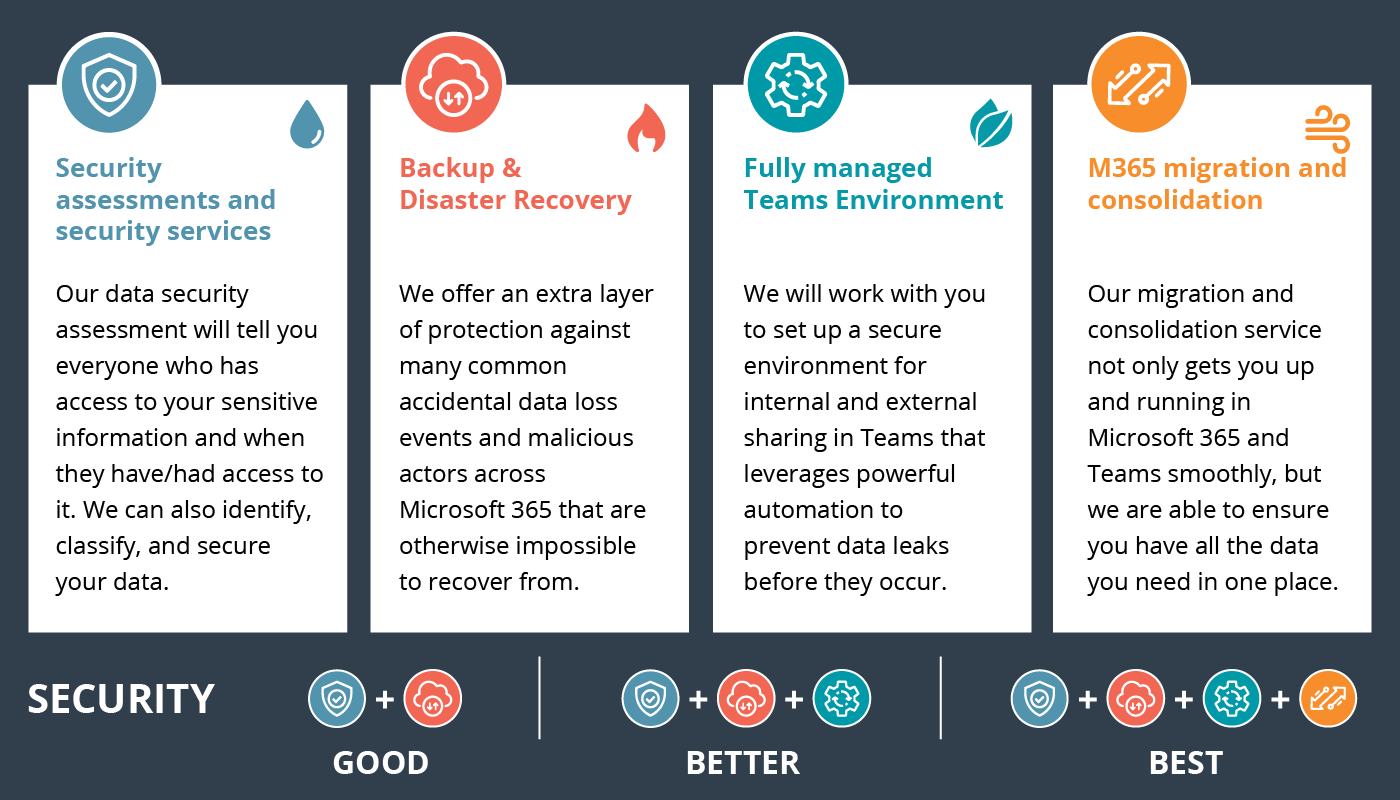
The M365 Risk Assessment is a comprehensive audit of your Microsoft 365 environment. It involves an automated assessment strategy that probes the entirety of your environment against the strictest settings from a comprehensive policy toolset. This approach provides insights into potential security and collaboration vulnerabilities, offering recommended action steps to secure vital business assets without constricting essential collaboration tools.
Identity and Access Management
Identity and Access Management (IAM) ensures that the right individuals access the right resources at the right times for the right reasons. It includes managing user identities, authentication, and access policies to protect your organization's data and resources. IAM solutions like Azure Active Directory provide single sign-on, multifactor authentication, and conditional access to enhance security.
Data Loss Prevention
Data Loss Prevention (DLP) helps you protect sensitive information from being shared or accessed by unauthorized users. DLP policies can dynamically prevent unauthorized use by identifying, monitoring, and automatically protecting sensitive data across Microsoft 365 services. This ensures that sensitive information is not accidentally or maliciously shared.
Defender for Endpoint
Microsoft Defender for Endpoint is an enterprise endpoint security platform designed to help enterprises prevent, detect, investigate, and respond to advanced threats. It provides advanced threat protection, endpoint detection and response (EDR), and automated investigation and remediation capabilities to secure your endpoints against sophisticated cyber threats.
Email Security
Email Security solutions protect your organization from email-based threats such as phishing, spam, and malware. These solutions include features like email encryption, advanced threat protection, and anti-phishing measures to safeguard your email communications and prevent data breaches.
Backup and Recovery
Backup and Recovery solutions ensure that your data is protected and can be quickly restored in the event of data loss or a disaster. These solutions include backup for Mailbox, OneDrive, and SharePoint, allowing you to recover individual files, folders, or entire systems to maintain business continuity.
User Awareness Training
User Awareness Training is crucial for educating employees about security best practices and how to recognize and respond to potential threats. Regular training sessions and simulated phishing attacks help build a security-first culture within your organization, reducing the risk of human error leading to security incidents.
Compliance Management
Compliance Management helps organizations meet regulatory requirements and manage data governance. Solutions like Microsoft Purview provide tools to assess, monitor, and ensure compliance with various regulations, helping you manage risks and protect sensitive information.