In Part 3 of the "Phishing Attacks and Recommended Solutions to Protect Your Organization" webinar we are going to be reviewing Office 36's Anti-Phishing solution– Office 365 ATP. We will be reviewing Platform Type, Requirements to Implement, Security Measures – Safe Attachments, Safe Links, Anti-Phishing, User Training, and some other considerations, including integration with other services.
Office 365 ATP is a cloud-based email filtering service that helps protect your organization against unknown malware and viruses by providing robust zero-day protection; and it includes features to safeguard your organization from harmful links in real time. It operates on the SaaS Platform or Software as a Service platform. This service requires Azure Active Directory, which is automatically included with Office 365 Exchange online mailboxes; and it can be configured for on-premise Exchange Server or other on-premise SMTP email solutions.
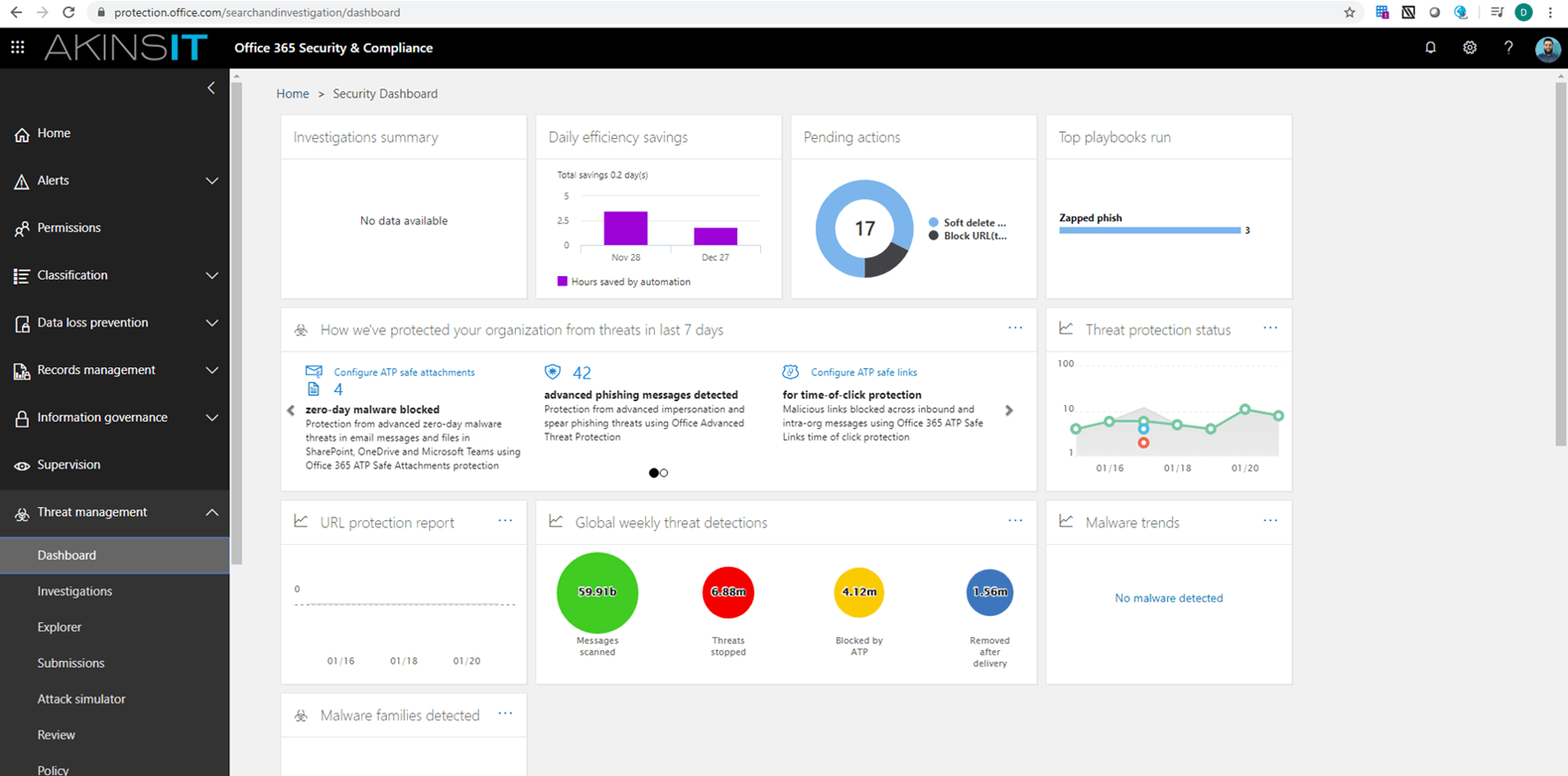
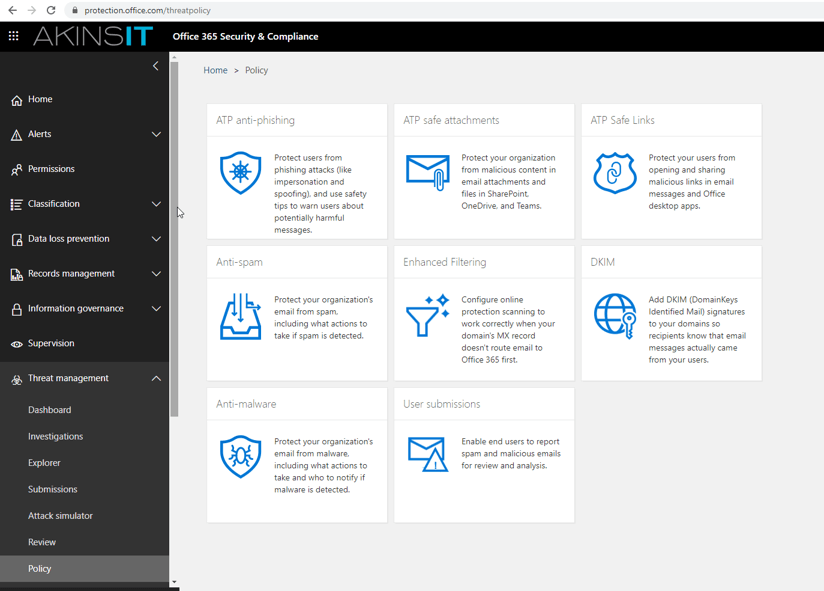
By heading to Office 365 Security & Compliance center > Threat management > Policy, you are presented with the O365 ATP Suite. We will be reviewing safe attachments first.
ATP SAFE ATTACHMENTS
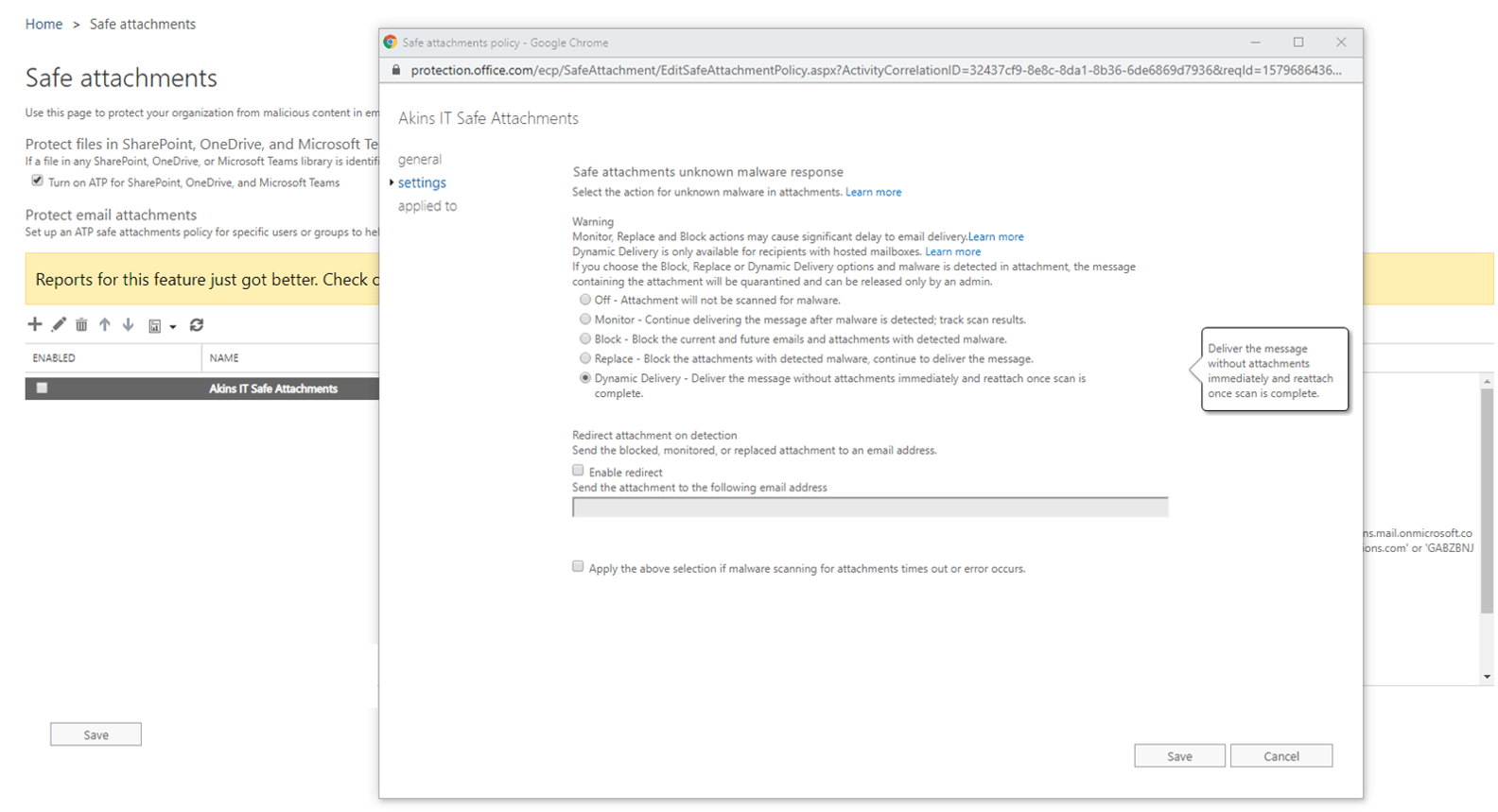
ATP safe attachments provides zero-day protection to safeguard your messaging system by checking email attachments for malicious content. It routes all messages and attachments that do not have a virus/malware signature to a sandboxing environment, and then uses machine learning and analysis techniques to detect malicious intent.
You can configure this policy to
- Monitor – which only tracks scan results.
- Block – which blocks the whole email and malicious attachment all together.
- Replace – which delivers the email but removes the malicious attachment.
- Dynamic Deliver – which avoids message delays while still protecting recipients from malicious files. It does this by delivering the email without full attachments immediately and reattaches once the scan is complete. One element you don’t see in this configuration screen with Dynamic Deliver is the preview function which, for most PDFs and Office documents, can be viewed in a safe mode while ATP scanning is underway.
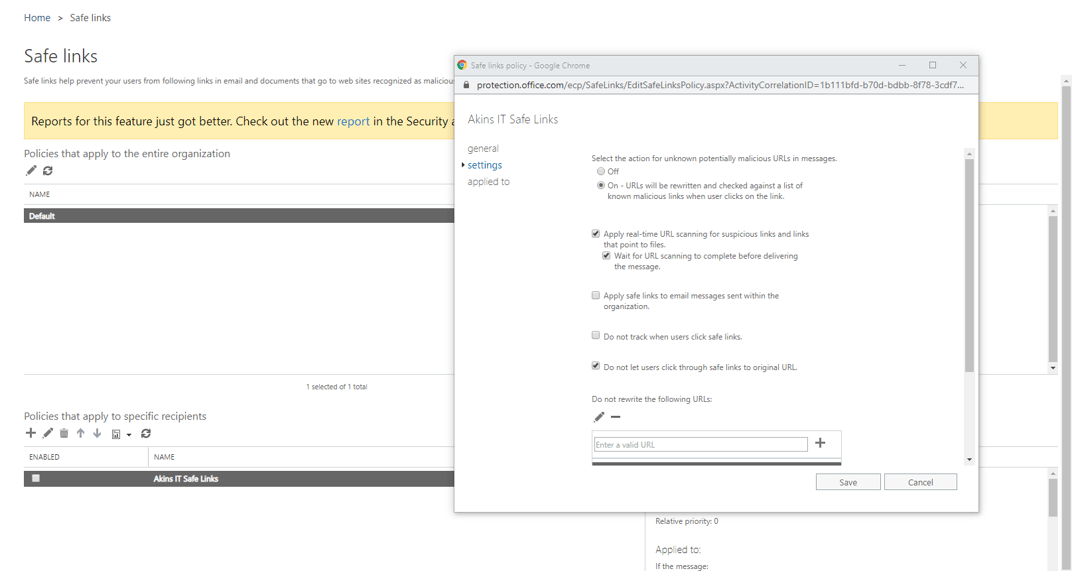
ATP SAFE LINKS
In the image below, you see Safe links which provides time-of-click verification of URLs, for example, in email messages and office suite files. Protection is ongoing and applies across your messaging and office environment including other Office Applications such as Word, Excel, PowerPoint. Safe links remain accessible and malicious links are dynamically blocked. For end users in your organization, you are able to control if scanning is complete before delivering messages to users or for real-time scanning.
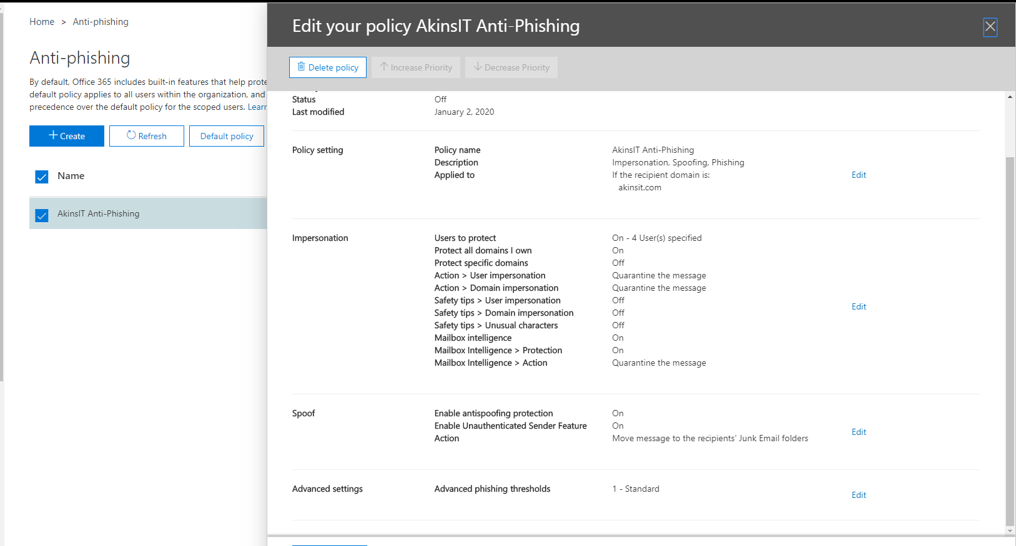
ATP ANTI-PHISHING
With the Anti-Phishing policy, you have the ability to protect attempts to impersonate your users and organizational domain. It applies machine learning models and impersonation-detection algorithms to prevent phishing attacks. This actually works in conjunction with Safe Attachments and Safe Links, and therefore, multiple machine learning models, to analyze the message to determine if this policy applies to the message and the appropriate action is taken.
Anti-Phishing also enables Mailbox Intelligence, which monitors user’s email habits and personal contacts. It also identifies unusual activity like sending an abnormal amount of mail or data during unusual time periods, which could be a key indicator of a data exfiltration. When this Is triggered, you then can determine what will occur automatically by the Mail Intelligence > Action found here.
USER TRAINING
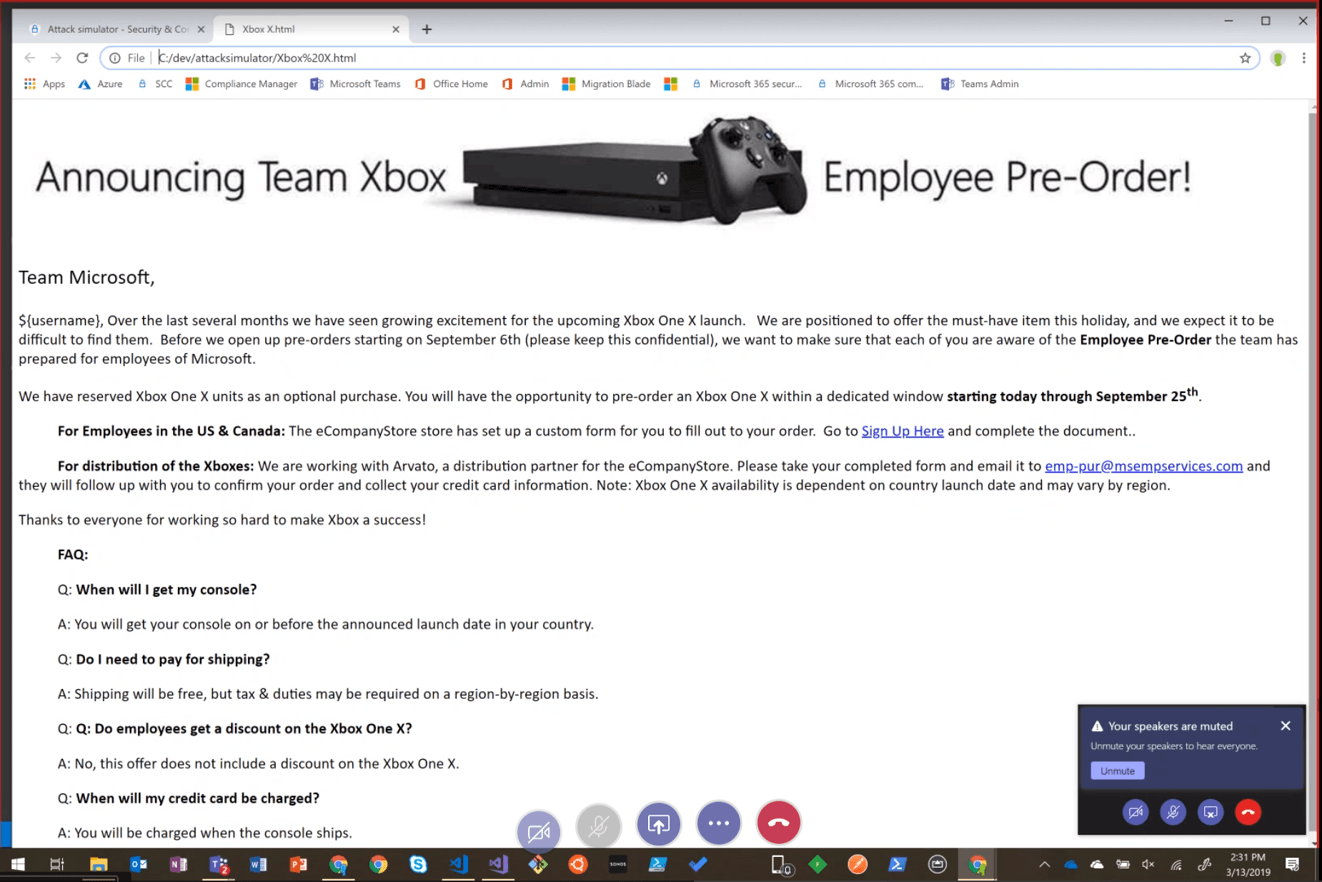
In terms of user training, Microsoft provides capabilities to train users in a more direct manner with Attack Simulator. In this simulator, you are able to run realistic attack scenarios in your organization that can help identify and find vulnerable users.
Some attacks you are able to create include:
- display name spear-phishing attacks
- password-spray attacks
- brute-force password attacks
This feature is unique in that you are able to create a custom, reusable email template specific to your organization. You may be surprised to learn that Microsoft actually used this internally when developing Attack Simulator with the Xbox One X launch and an a “employee Pre-Order” offer. It was reported with a 60% click rate.
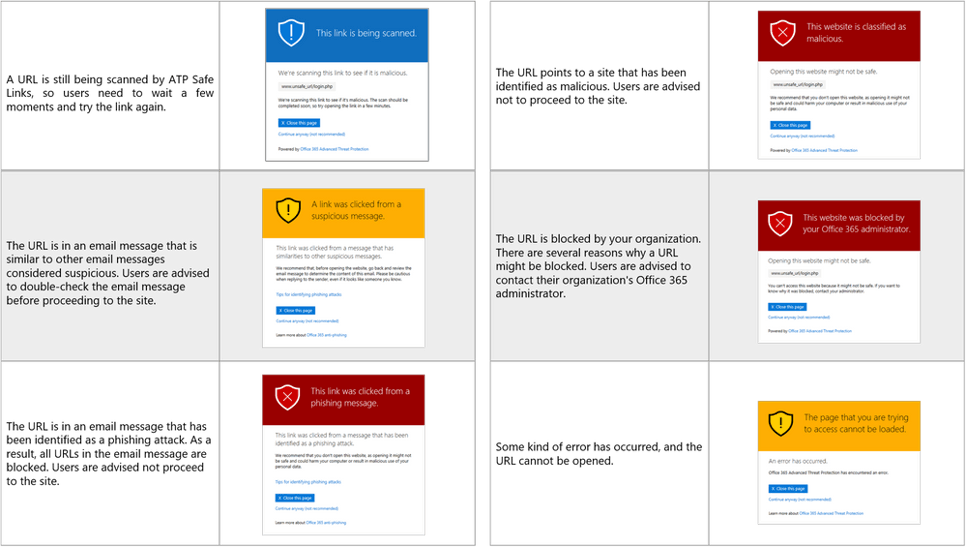
Similarly to other solutions, URL protect also provides an element of user training here with indicating when URLs were detected to be malicious.
OTHER CONSIDERATIONS
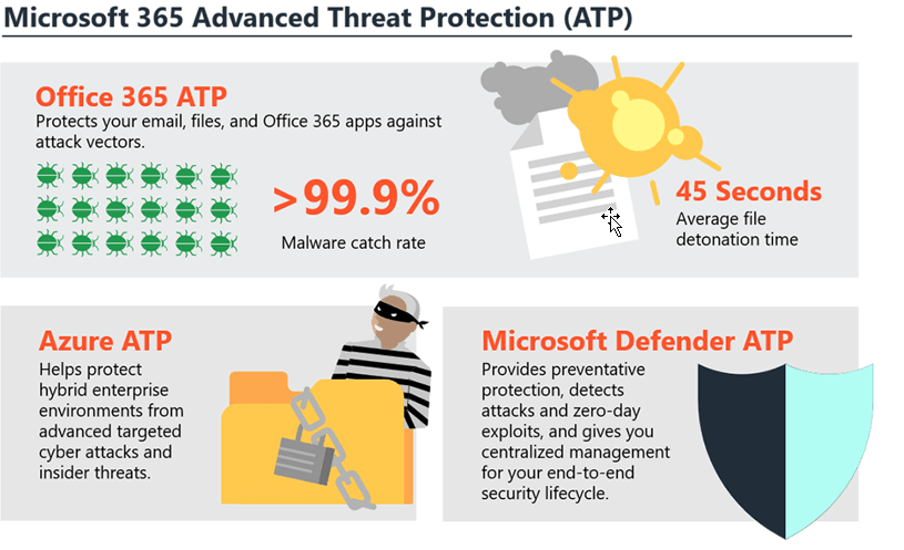
One of the key elements to Office 365 ATP is not only its focus on email security, but Microsoft also provides telemetry with other ATP solutions such as Defender ATP and Azure ATP in the Microsoft 365 Ecosystem. The true benefit here is the built in, not bolt on, approach that no other vendor is able to provide. Advanced Threat Protection works 24/7 and provides automated investigation and response.
One example of this would be Malware ZAP– if malware is weaponized after being delivered to users it will remove previously delivered messages and initiate an automated investigation to determine who else may be impacted or was delivered the same payload.
Another consideration with Office 365 ATP would be User Submission with the Report Mail add-in that is dynamically added to outlook for end users when enabled. This provides the ability for users to submit emails as junk or phishing - which with admin approval will allow automatic investigations to increase your cyber security overall.
ADVANTAGES
Some advantages you find with Office 365's Anti-Phishing solution is the ability to quickly enable and protect users, Automated investigation & Remediation, User Submissions. However, there can be improvements on the granularity of controls.
CONCLUSION
If you found the above information valuable and would like to see how Office 365 can enhance your email security in your organization, contact us.