How Local Governments Can Prevent Security Breaches
As an IT Director or IT Manager for a local government agency, you're responsible for ensuring the security of sensitive data and systems. Security breaches can have serious consequences. So it is critical to take proactive steps to prevent them. Cyber attacks, in general, happen every 39 seconds.
Cyberattacks on state, counties, cities, and tribal government IT infrastructure continue to occur. Local governments are especially susceptible because of the large amounts of direct data they store that can be linked to their constituents.
While there are specific strategies that
local government IT staff can implement, there are also a few simple measures you could take now. These measures can help to form a foundation of a secure IT infrastructure.
Establish Clear Cyber Security Policies and Procedures
One of the most important steps you can take to prevent security breaches is to establish clear cyber security policies and procedures. The design of these policies should
protect your community's data from various threats. These threats will often include malware, ransomware, and phishing attacks.
They should also include protocols for reporting and responding to security incidents. Regular observation and modification are necessary, and mistakes can happen by not doing this regularly.
Implement Comprehensive Security Solutions
To protect your community's data from cyber attacks, you need to implement comprehensive security solutions to safeguard your IT infrastructure. These solutions should be able to help protect your IT environment end to end. It would help if you were implementing IT security solutions such as the latest firewalls, antivirus software, and spam filters.
They should also include utilizing proven intrusion detection and prevention systems (IDS/IPS). This helps protect your network from unauthorized access. Working with a professional organization specializing in government IT solutions can streamline the process.
The best way to stay on top of cyber security would be to create a security-focused culture. That culture should align with the latest and proven cyber security measures.
Local governments are always at a high risk of attacks. Because of this, establish ongoing cyber security coordination and monitoring. This is where governments would benefit from appointing a cyber security point of contact (POC). Aside from one person, you could even have a designated council for cyber security, especially if the local government agency has already experienced attacks before.
Additionally, recognize the importance of policy. This is an easy way to increase the chances that employees will comply.
Any guidelines or standards you come up with, add them to your policy. Include it within all training and education materials as well.
Business Continuity and Backup Solutions
Make sure you have a robust backup and disaster recovery solution in place. A backup and recovery solution that backups your data on a continuous basis and allows for easy recovery of all of your data in a timely fashion will help your agency get back up in running quickly and avoid paying any ransom fees if you get hit with a ransomware attack.
Train Your Staff on Cyber Security Best Practices
It is essential to train your staff on the best practices for protecting the community's data. This includes training them to spot phishing attacks and use strong passwords for accessing critical applications and systems. Additionally, teach the staff how to protect their devices from malware and ransomware.
This training will also often involve other methods of educating workers. An example could be reinforcing confidentiality and training your staff on how to protect their personal devices that may access your IT infrastructure.
Another good practice is to train your staff on how to access agency resources via a VPN and how to enable full-disk encryption on personal computers that may access our IT environment.
Regular Updates to Your Software and Hardware
One of the best ways to protect your community's data is to keep your software and hardware up-to-date. This includes your operating systems and applications. You should also update your antivirus software, firewalls, and IDS/IPS systems.
Software updates often go overlooked as being necessary and essential. The thing is, software updates are crucial for making sure your IT systems are less vulnerable.
When going through an update, you're installing the latest features of your devices. Many of those feature updates involve security. If your software or hardware is outdated, you risk being vulnerable to cyber attacks.
Your desktop, laptop, and server operating systems should continually be updated with the latest patches. There may be times an update can't happen right away. If this happens, schedule it at the earliest time you can implement the update.
Create a Contingency Plan
If a security breach does occur, it is vital to have a contingency plan in place. This plan should include procedures for responding to the security breach and providing guidance on mitigating the damage caused by the attack.
The plan should serve as a solid form of risk management. Having this type of plan is a proactive measure. It can help local governments alleviate the issues they could run into when an attack occurs.
Your contingency plan should include specific instructions. It should also have processes and recommendations for staff to recover IT services and any lost data.
If you experience an interruption in the system, there should also be a plan in place to respond to the interruption with close observation.
Protecting Personally Identifiable Information (PII)
Another important step you can take to prevent security breaches is to comply with PII (Personally Identifiable Information) regulations. This will help ensure the privacy and integrity of your user's data. It will also help to ensure the overall safety of the agency's employees and citizens.
For California local government agencies, get familiar with the
California Consumer Privacy Act (CCPA) and implement best practices relevant to your agency. This act primarily targets consumer businesses, but it does not hurt implement the recommendations of CCPA.
Direct Strategies
As far as direct strategies go, there are a few things that local governments can start implementing right away. One of the most overlooked options is to create detailed training manuals.
These manuals would get directed towards employees. They are also often included in the onboarding process for new employees. Expand on this by offering regular education about security.
Proper information handling often goes overlooked. However, this is just as important. The main goal here is to ensure that your employees know how to identify potential threats.
Make sure that employees aren't sharing passwords. They shouldn't be accessing any insecure networks on government equipment either.
Local governments can work to create more secure cyber ecosystems. This involves looking at the security infrastructure as a whole.
You may need to modify the system to promote efficiency and safety. Having an assurance framework is another helpful option.
Additionally, local government agencies will benefit from securing any E-governance services. The same goes for working to strengthen regulatory government frameworks.
What Do These Security Breaches Mean For the Public?
A government data breach often leads to a significant financial loss. These losses can be a big hit to local governments.
According to the Cost of Data Breach Report of 2021, the cost of data breaches on a global scale in public sectors went up to 79%. That was between 2020 and 2021.
Additionally, in 2021 alone, at least 281.5 million people were affected by a data breach in some way. This drives towards local governments.
They are often seen as targets because of the amount of highly sensitive information they store. That said, think of all of the places surrounding a local government. Communities are made up of multiple organizations that house sensitive and personal information of citizens.
Take hospitals or healthcare facilities, for example. If you look into data breach cases of hospitals, or healthcare facilities, you will come across quite a few. Take a hospital in Minnesota into consideration. Focus on how they suffered a data breach that affected at least 49,351 people.
Employee email accounts were able to be accessed by external sources. This puts various forms of personal data at risk.
Some of those forms of personal data were names and dates of birth. Medical record numbers and even addresses were also compromised. There was even more at risk for privacy violations as well.
More About This Breach
Additionally, there was direct clinical-based information such as treatment details and medical diagnoses. Health insurance information was also uncovered.
When a cyber-attack happens, these are the things that communities can become vulnerable to. Individual privacy is wholly compromised when a data breach takes place.
This is especially true when considering that Social Security numbers were also compromised. So were driver's license numbers and other forms of personally identifiable information.
You can also consider private and public schools and smaller entities within a community that might house personal information.
Keep in mind that there are other security measures you can take. Local governments can work to improve cyber forensics. This helps to prevent crimes and to quicken any open investigations.
Consider having an advisory or alert system that can broadcast across devices.
Cyber Threats That Local Governments Are at Risk For
Any government is vulnerable to various cyber-attacks. One of the most common types is ransomware attacks. Unfortunately, different local governments are always under cyber-attacks such as this.
They also include phishing, brute force, vectors within emails, and direct hacking. Local governments are at extreme risk of data leakage and insider threats. No local government is safe from cyber-attacks.
Understanding that the government isn't immune is the first step to forming proper security measures. It's safe to say that government cyberattack exposures are not entirely new risks. They are often more persistent given what local governments hold and have access to.
At least 44% of ransomware attacks on a global scale were targeted towards municipalities in 2020. Although most of the attacks were ransomware attacks, the risk is still high for other types.
For example, SQL injections and password attacks pose a threat. Distributed denial of service (DDoS) do as well.
Security Threat Trends
There are still many cyber security threats that local governments will need to pay attention to in 2022. Remote work is becoming more prevalent. This leaves many employees more susceptible to having their equipment or networks hacked.
Some vulnerabilities can come with almost anything that you use on different networks. Protecting residents from security breaches should be a focus for local government IT departments. It should be because when the government is susceptible to cyberattacks, all of its citizens are as well.
The same goes for other organizations within the community that might also hold or has access to personal information. It would help if you also watched out for double extortion ransomware attacks.
Additionally, ensure that you are paying attention to data privacy. Unfortunately, 2022 still shows signs of continued high-level security threats.
This is especially true with the current economic state. It's also, all the more reason to implement multi-factor authentication options. Expanding on this and improving different authentication methods are great tactics.
They ensure that employees have secure networks when remote working can also help. This alleviates potential issues local governments could run into.
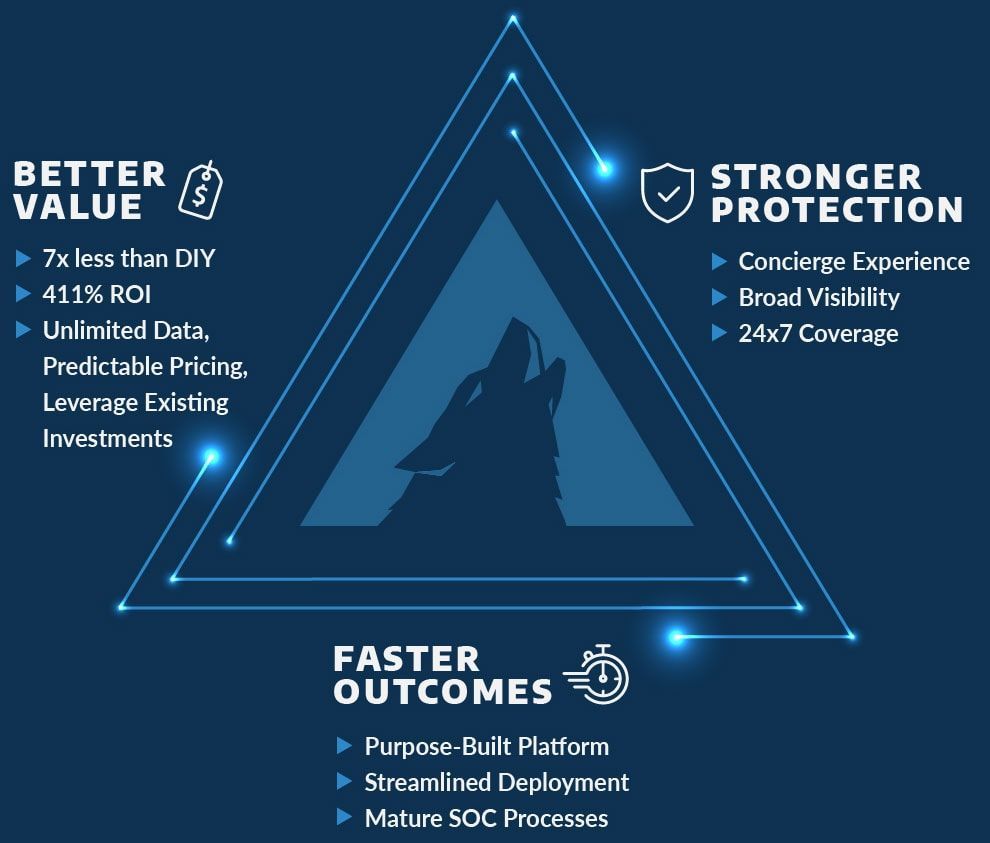
Get Custom Solutions
If you need
government and
education IT solutions, consider working with Akins IT. By focusing on finding the right solutions for your organization, you alleviate the potential of wasting resources and time.
Realizing how local governments can prevent security breaches is a proactive measure. By allowing industry-educated experts to tailor technology solutions to suit your IT infrastructure, you can quickly increase your levels of security and strengthen proactivity.
Are you interested in learning more and hearing about our proven success? Contact our team today to see how we can help.